Not long after IBM sold its Thinkpad laptop division to a Chinese company in 2004, the State Department issued a ban on the laptops from being on the agency's network citing security risks from it being foreign-owned.
Over the next two decades, the company would be a regular security concern, not just for its foreign ownership, but for having compromised security on its computers that would expropriate user data.
The U.S. government has repeatedly highlighted the efforts of Chinese state-sponsored actors trying to infiltrate government networks, and there are indications that Lenovo products came with backdoors that could enable this. While Lenovo is one of the top-selling laptop manufacturers, it is also partially owned by an entity related to the Chinese military.
While those computers would be restricted in various ways from certain agencies and certain circumstances, they have never had an outright ban like that of manufacturers like Huawei, ZTE, or Kaspersky.
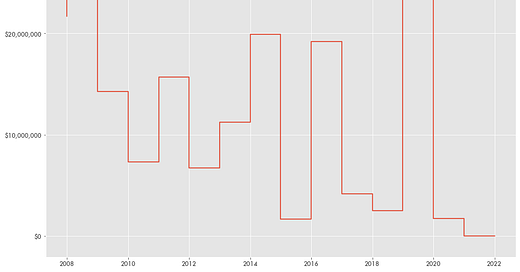
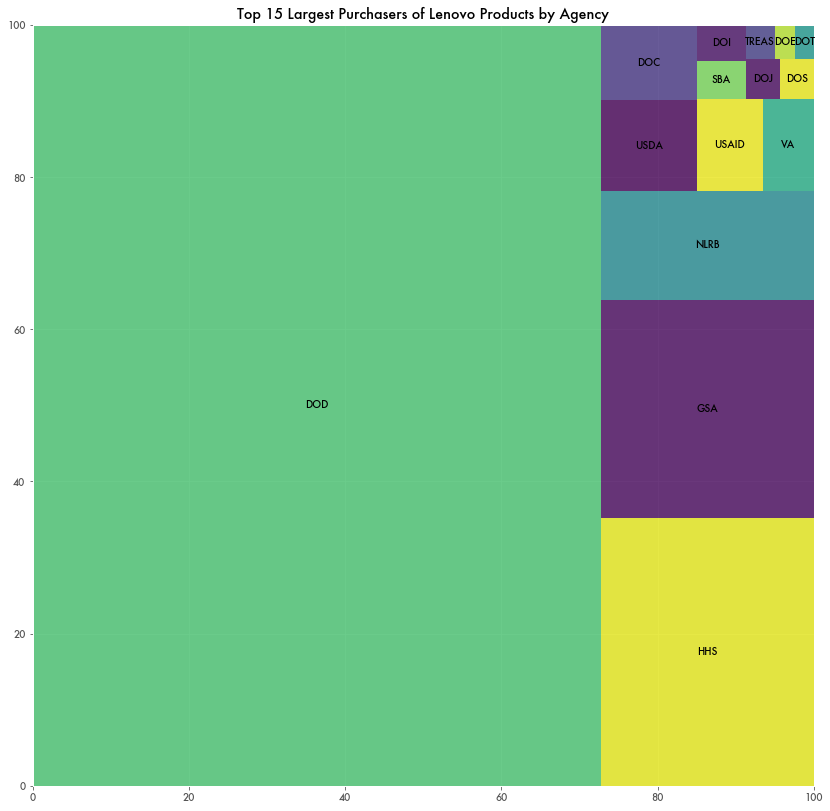
And the U.S. government continues to buy Lenovo laptops in bulk. According to contract data from USA Spending, the government bought around $37 million worth of Lenovo products in 2020, with the larger majority of that being a $17 million expenditure for the Department of Defense.
History of Security of Concerns
In 2006, the State Department bans Lenovo computers from their network.
After MI5 identified “backdoors” and vulnerable firmware in Lenovo products, their computers are banned from the intelligence networks of all Five-Eyes countries: Australia, Canada, New Zealand, United Kingdom, and the United States.
In 2008, Lenovo laptops are removed from use by the Marine Corps in Iraq because they were reported to be transmitting data to China according to testimony from a 2010 lawsuit related to counterfeit Cisco products.
In 2015, it was discovered that ad software called VisualDiscovery came pre-installed on Lenovo laptops which would transmit browser data to an external source using the computer's firmware, something that the computer's manufacturer ostensibly would be complicit in enabling. The software, made by an Israeli company Superfish, routed all web traffic through servers controlled by Superfish.
The Federal Trade Commission (FTC) brought charges that the compromise harmed consumers. Lenovo would eventually settle a class action lawsuit with state attorneys general for $3.5 million and another class action lawsuit for $7 million.
When Lenovo purchased IBM's x86 server technology in 2015, the change to foreign ownership meant that the Navy, which used those servers for ballistic missile guidance, had to immediately replace the computers at a cost of $378 million.
A 2016 email from the Air Force's Cyber Command indicated that Lenovo products were being removed from the approved products list, only to have that statement rescinded. Instead, only networking equipment like routers were being removed, not personal computers like laptops.




It is a shame that it seems money (and not anything to affect salaries of those making these decisions) is controlling our cybersecurity and not sound evaluated information. Many time driven by the contractors since there is no real checks n balances of qualifications and contractor power.